Introduction
Hello and welcome to the functional programming challenge write up from UTCTF 2021.
If you are only interested in the exploit code, see here.
Scenario
This challenge invites you to enter a list and then choose to apply a map or filter
on this list.
For that, it gives you the addresses of those functions and wants you to select
the one that will be executed.
Here an example of execution :
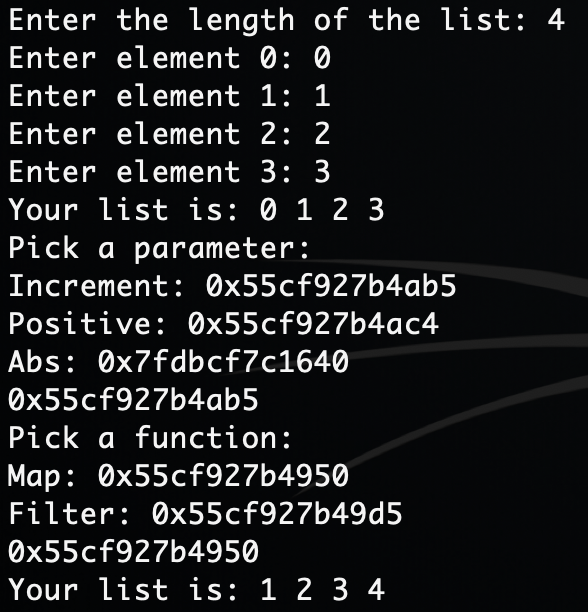
Exploit
You can enter the function pointer you want so that’s how we will have RCE (Remote code Execution).
So let’s take a look at checksec :
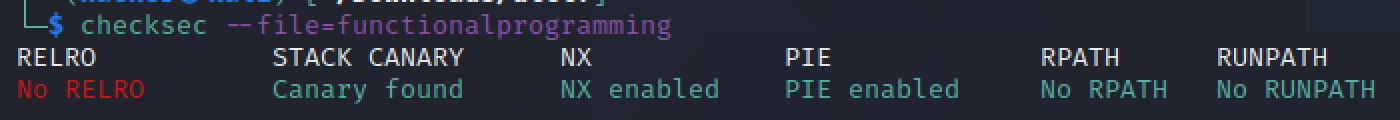
The input array is on the stack but NX is enabled so the challenge is not about shellcoding. There is a stack canary but this it is neither about overflows.
In fact if we take a look at the function addresses we can apply by mapping or filtering,
there is a noticeable difference for the abs function address
Here an example :
1
2
3
Increment: 0x5579b5eebab5
Positive: 0x5579b5eebac4
Abs: 0x7fb5132c8640
In fact abs is a libc function.
So we have a given libc leak.
Now all we need to do is to use a libc database such as this website
to find the offset with the system libc function.
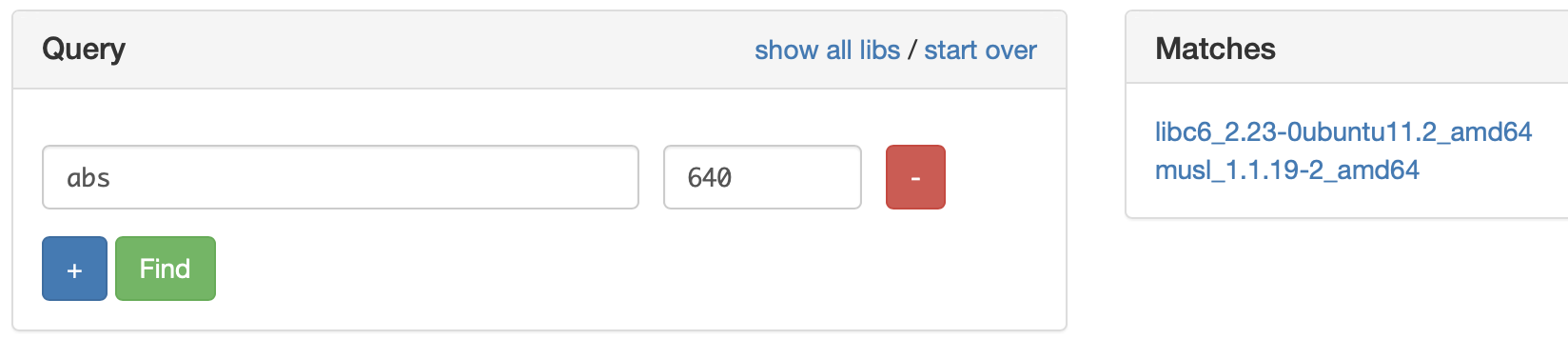
We just have to fulfill our array with /bin/sh (you have first to convert it into a int list)
And we are done !
The flag was utflag{lambda_calculus_pog891234}.
Thanks for reading !