Introduction
Hello ! This week I have enrolled in the Shakti CTF with the LSE. We managed to get to the second place ! Here are some Write-Ups from the challenges I solved !
Pwn
Birdie: 100pts
The goal is to defeat the canary. We already have a function giving a shell in the binary.
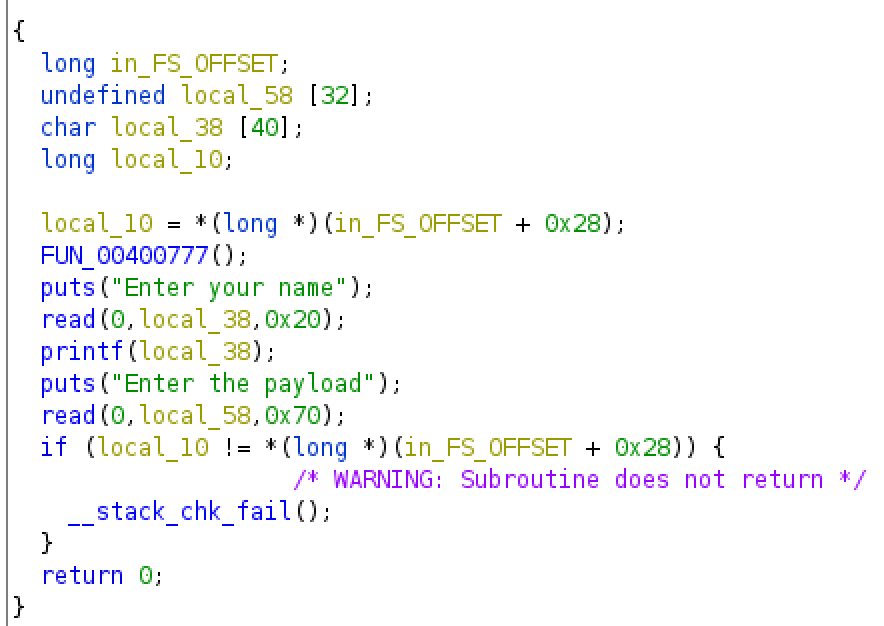
The buffer overflow and the format string vulnerabilities are pretty easy to see. With gdb we see that we must input
1
%15$p
to leak the canary.
We then just have to send offset + canary + shell_address.
Here is the script.
Flag: shaktictf{c4tch1ng_th3_birdie_w4s_e4sy_pe4sy}
Cache_7: 400pts
This challenge was hard and was a first Use-After-Free/Double-Free vuln for me. Hopefully the challenge was straightforward.
I managed to have a libc leak, and had a way to write where I wanted but the heap was too unstable to do both.
I adapted this Write-Up on a very similar challenge. Here
My script here.
Flag: shaktictf{u_4re_a_trU3_c0mr4de}
Reverse
MargaREt: 300pts
The first time I took a look at the binary, I saw it was in Go and directly gave up.
But then, I came back to it.
First thing I did is running strace and saw something quite interesting.
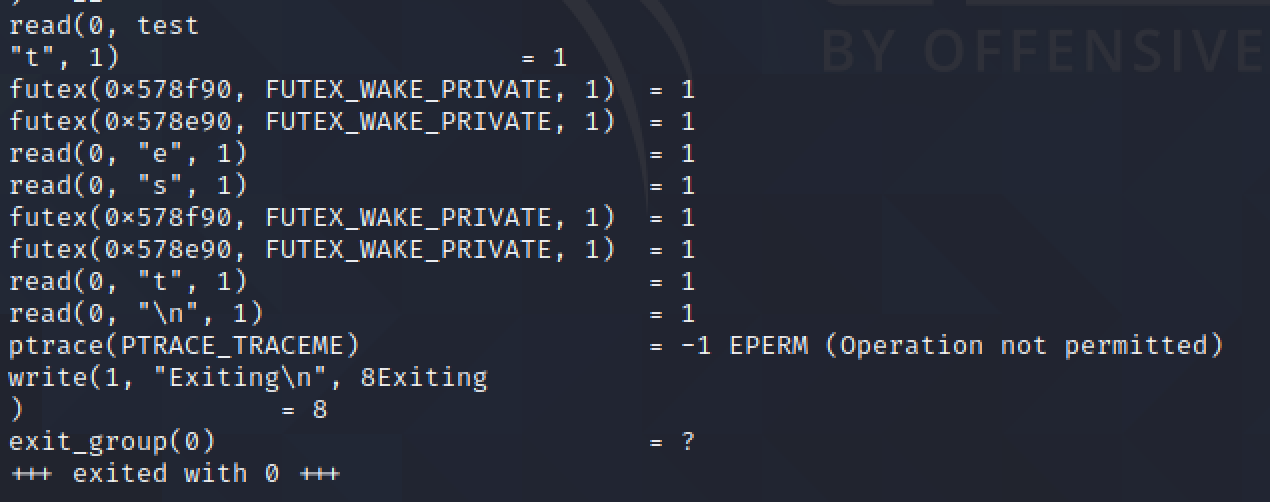
We can see that even if I gave test as input, the binary read it char by char.
So my idea was to sort of bruteforce the flag character by character.
To do that, I need to understand how the binary processes each characters.
But in fact I did not need to.
By trying to run the binary with the prefix shaktictf{ I did not get the usual Try harder message.
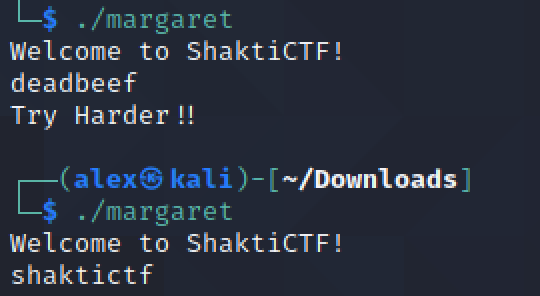
Any substring of the flag would not return an error. So I simply bruteforced it char by char, looking at the error message.
I really do not know what was the intended solution, because 300pts for that is quite large.
Here is the script.
Flag: shaktictf{0ur_4str0naut5_d1d_n0t_hav3_much_t1m3_but_7hey_h4d_marg4r3t_H4m1l7on!}
Fusk: 100pts
This challenge consists of a XOR between an int array and the result of a recursive function.
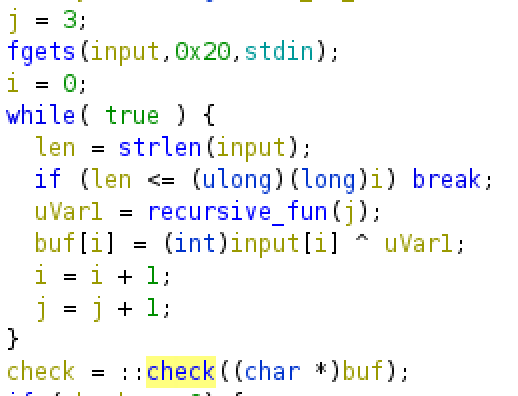
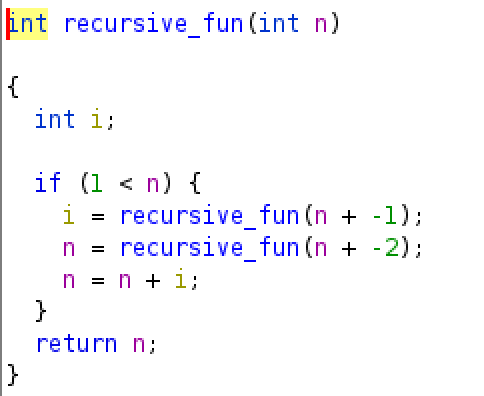
I dumped the int array, wrote the function in python, XORed everything back and voilà !
No need to optimize that greedy function by the way.
Here is the script.
Flag: shaktictf{s1mpl3_movfu5ca7i0n}
Misc
decodeit: 100pts
This chall is pretty straightforward. We have a barcode.

I found this website to decode it : zxing
Flag: shaktictf{N1C3_w0rK_Fr13nD}
Follow-Up: 50pts
In this one we are given a pcap.
I threw it in Wireshark and directly saw some pastebin links in clear.
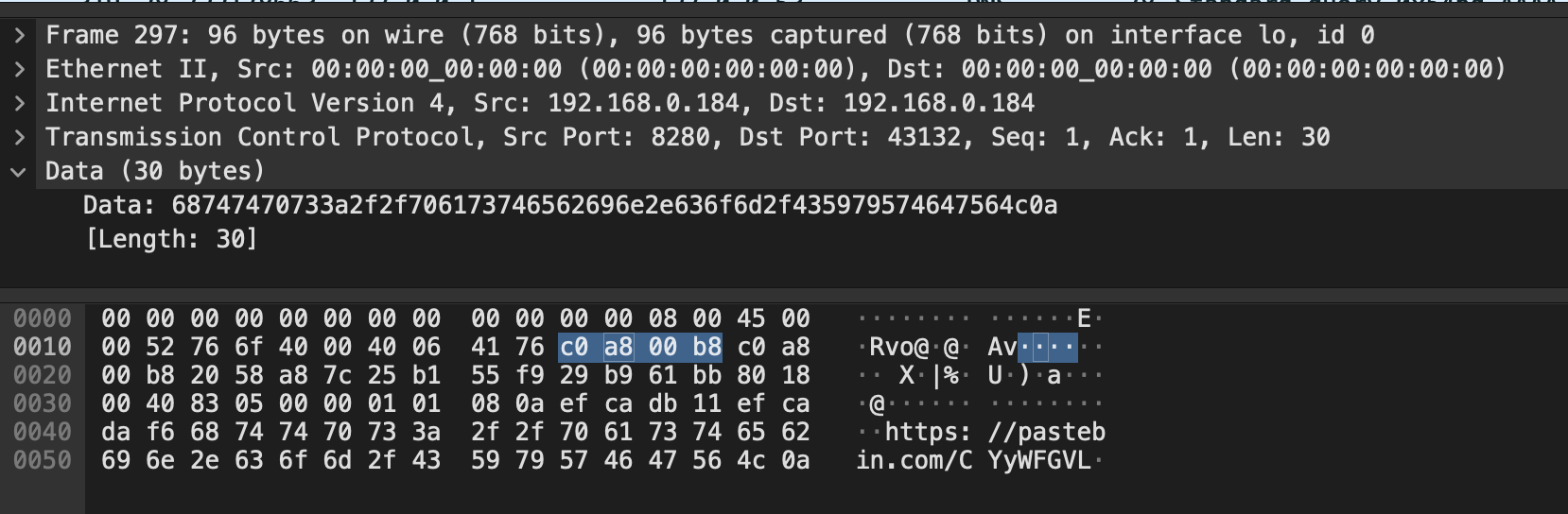
This one led me to a fake flag.
I wanted to be quick on that chall so I tried to run strings on the file. I got lucky and found the other pastebin link containing the flag.
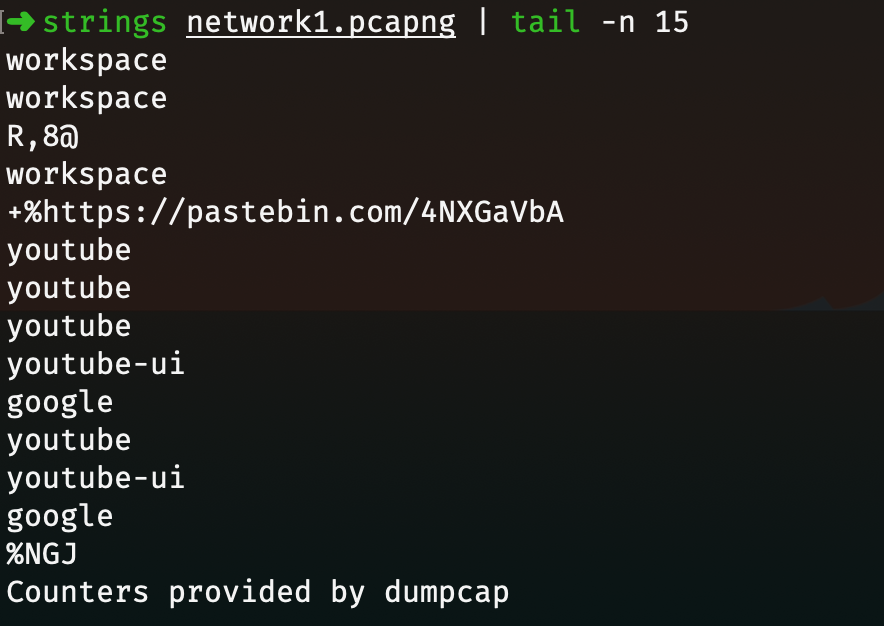
Flag: shaktictf{Th15_w4s_eA5Y!!}